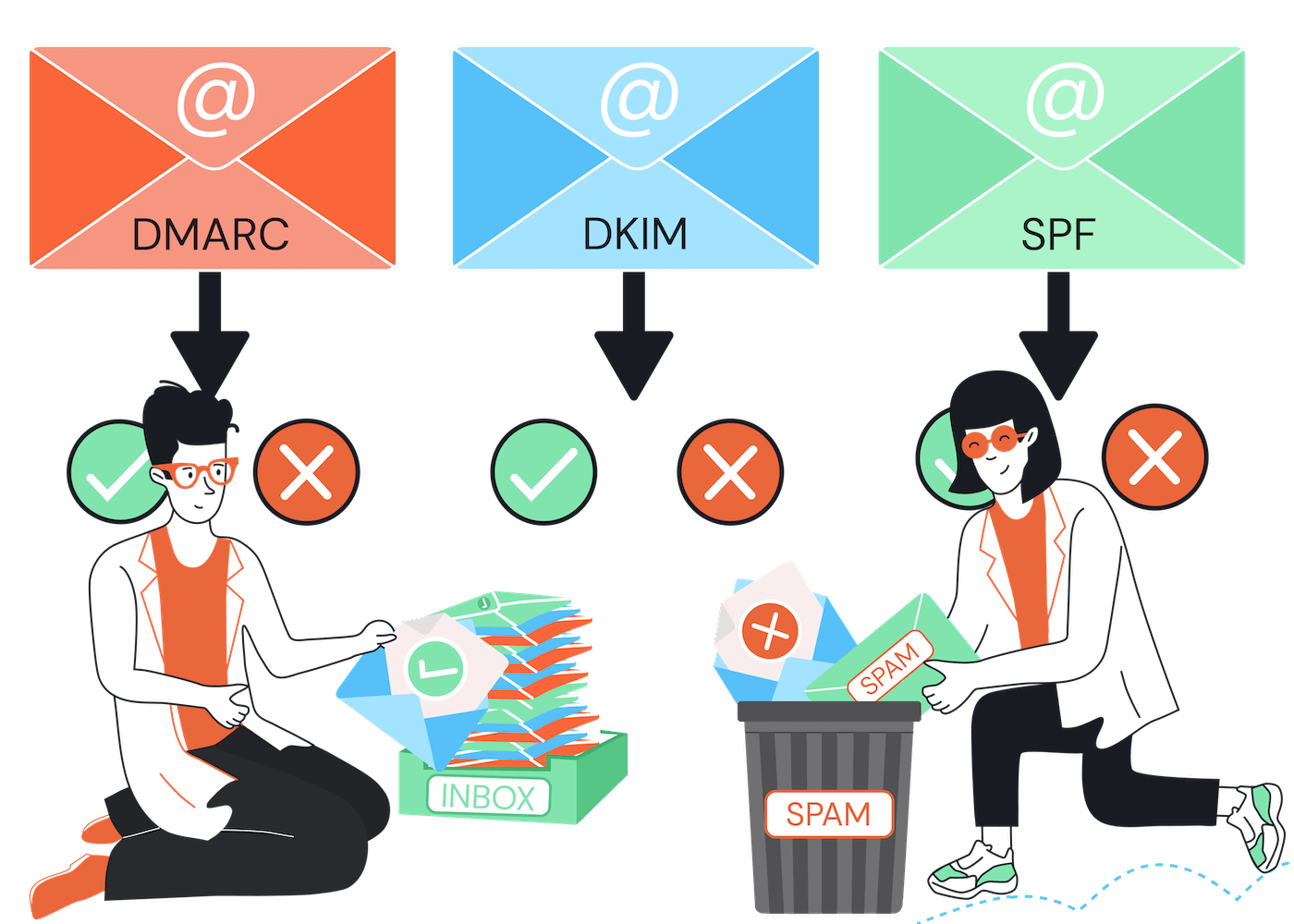
DMARC, DKIM, and SPF are all email authentication methods used by senders to combat email spoofing and phishing attacks. While you could use SPF and DKIM independently, you can’t use DMARC without also using at least one of the other methods.
And the truth is: if you’re an email marketer, that’s sending emails to hundreds or thousands of people, you need to implement all three methods together to achieve respectable levels of authentication and deliverability.
That’s because each method works differently, with its own strengths and weaknesses, and it’s only when they are implemented together that you will achieve comprehensive protection.
Let's look at each one in turn and compare them…
SPF (Sender Policy Framework)
SPF is an email authentication protocol that verifies the sender's IP address. It allows domain owners to specify which mail servers are authorized to send emails on behalf of their domain.
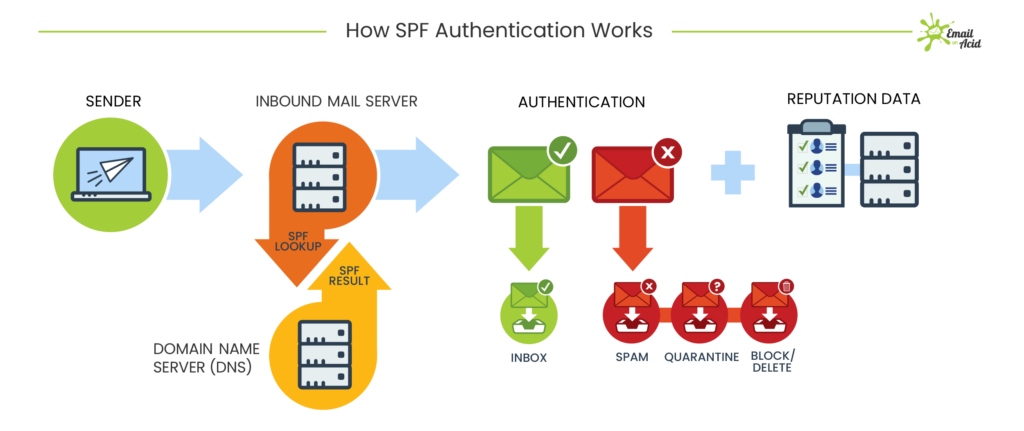
How SPF Authentication works – by EmailOnAcid
When an email is received, the recipient's email server checks something called the SPF record of the sender's domain. The SPF record is simply TXT record in the DNS settings that contains:
- A list of all IP addresses or hostnames of the mail servers that are permitted to send emails on behalf of that domain
- Policies for how receiving servers should handle emails from servers that are not on the list.
If the sender's IP matches one of the authorized servers listed in the SPF record, the email is considered legitimate and passes to the inbox. If not, then the email may be marked as spam or rejected outright, depending on the policy specified in the SPF record.
Strengths of SPF:
- Ease of Implementation: SPF is generally simpler to implement than DMARC and DKIM. It simply involves adding a TXT record to the DNS settings of a domain to specify the list of authorized mail servers. This simplicity can make it an attractive starting point for organizations looking to improve email authentication.
- Straightforward Authentication: SPF directly verifies the sender's IP address against the list of authorized mail servers. It provides a clear indication of whether an email originated from an authorized source.
- Reduces Spoofing: SPF helps mitigate email spoofing by allowing domain owners to specify which mail servers are authorized to send emails on behalf of their domain. This helps prevent unauthorized parties from impersonating legitimate senders.
Weaknesses of SPF:
- Dependence on IP Addresses: SPF relies solely on IP address verification, which can be problematic in scenarios where emails are sent through third-party services (e.g. Mailchimp). If the sender's IP address changes, the SPF record must be updated otherwise, legitimate emails may be rejected or marked as spam.
- No Message Integrity Verification: While SPF verifies the sender's IP address, it does not provide any assurance regarding the integrity or authenticity of the email content itself. It does not protect against email tampering or malicious content.
- Limited Flexibility: SPF records limit the number of DNS lookups allowed to ten, which can sometimes be restrictive for organizations with complex email infrastructures or multiple authorized mail servers. This can lead to issues if the SPF record exceeds the lookup limit, potentially causing legitimate emails to be rejected.
- Incompatibility with Forwarding: SPF can be incompatible with email forwarding services. When emails are forwarded, the original sender's SPF record might not cover the forwarding server, leading to SPF failures and potential email deliverability issues.
- Weak Protection from Advanced Spoofing: Attackers can use more advanced techniques to bypass SPF, such as spoofing the from address (which is what the user sees), while using a legitimate address in the return-path (which is what SPF checks).
Overall, while SPF provides a basic level of email authentication and helps mitigate email spoofing, it has limitations in terms of flexibility and effectiveness in certain scenarios.
Implementing additional authentication methods like DKIM and DMARC alongside SPF will enhance email security and provide more comprehensive protection against phishing and spoofing attacks.
DKIM (DomainKeys Identified Mail)
DKIM is another email authentication method, that adds a digital signature to the email message.
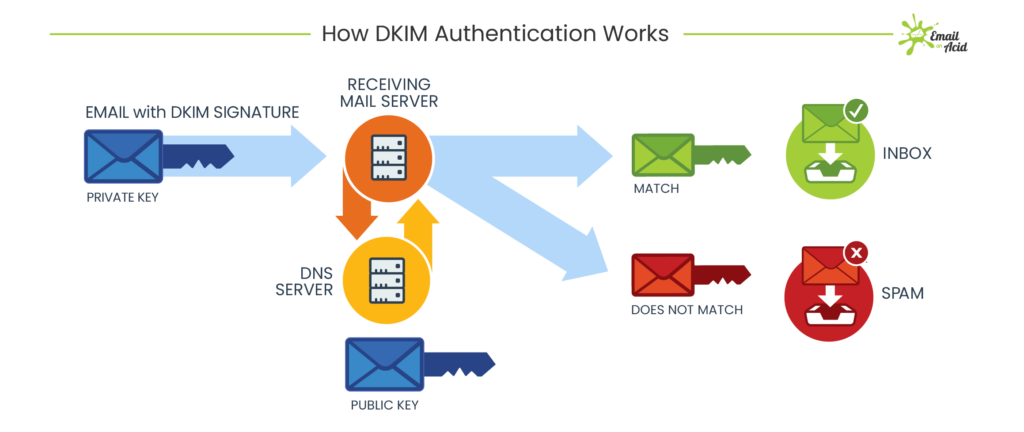
How DKIM works – by EmailOnAcid
This signature is generated using a private key held by the sending domain's mail server. The recipient's email server can then use the public key published in the sender's DNS records to verify the signature.
If the signature is valid, it confirms that the email has not been tampered with during transit and that it originated from the claimed sender's domain.
Strengths of DKIM:
- Cryptographic Content Authentication: Unlike SPF, DKIM directly verifies that the email content has not been tampered with during transit, adding a layer of security against email modification.
- More Compatible with Forwarding: While SPF validation checks the path the email took on its journey to the recipient, DKIM validation is based on the signature in the email headers. This means that while SPF can fail when the path changes (through forwarding), DKIM will still work.
- Improves Domain Reputation: Because DKIM signatures are domain-specific, they can help build a positive reputation for a domain among receiving email servers that validate DKIM signatures, potentially improving email deliverability over time.
- Flexibility and Control: DKIM allows senders to specify which elements of the email are covered by the signature, offering a degree of flexibility in how email authentication is implemented.
Weaknesses of DKIM:
- Lack of Policy Enforcement: DKIM alone does not specify what should happen if a message fails DKIM verification. Without a clear policy provided by DMARC, receivers might handle DKIM failures in various ways, potentially leading to legitimate emails being accepted even if they fail verification.
- Complex Setup and Management: Implementing DKIM requires generating keys, configuring email servers, and updating DNS records. This complexity can be a barrier for some organizations, especially those with limited IT resources.
- No Sender Policy Publishing: DKIM does not offer a way to publish sender policies like SPF does. SPF allows domain owners to specify which mail servers are authorized to send email on their behalf, reducing the chances of email spoofing.
- Limited Protection Against Certain Attacks: For example, it cannot protect against attacks where the attacker has legitimately compromised an email account within a domain that has DKIM set up. In such cases, emails sent from the compromised account would pass DKIM checks because they are technically legitimate emails from that domain.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC is a policy framework that builds on top of SPF and DKIM to provide domain owners with greater control over email authentication.
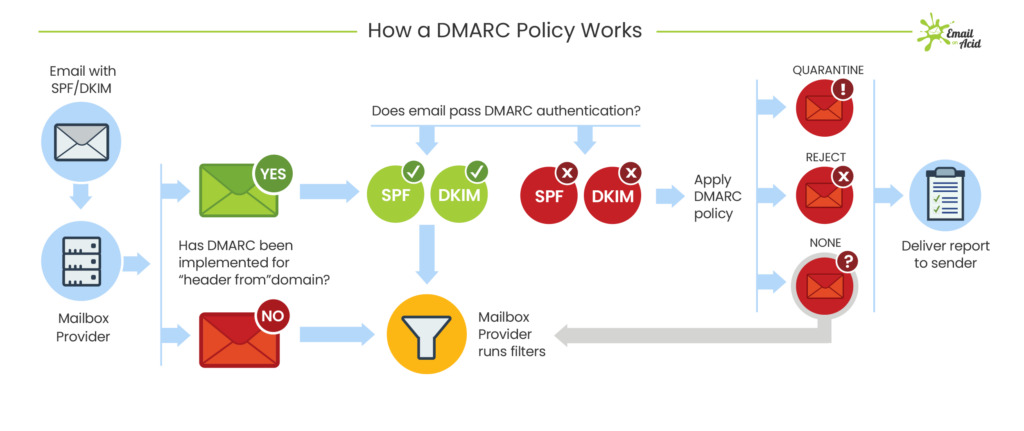
DMARC authentication process – by EmailOnAcid
DMARC allows domain owners to specify what action should be taken when an email fails SPF or DKIM authentication checks. This could include delivering the email, quarantining it in the spam or junk folders, or rejecting it outright.
This is controlled by settings within the DMARC record:
- p=none: Take no action
- p=quarantine: Deliver to the spam folder
- p=reject: Don’t send the message at all
Additionally, DMARC enables domain owners to receive reports about each email authentication failure, allowing them to monitor and improve their email security posture over time.
Strengths of DMARC:
- Policy Enforcement: DMARC allows domain owners to specify how an email should be handled if it fails SPF or DKIM checks. This means senders can instruct receivers to either quarantine or reject emails that don't authenticate, offering stronger control over how their emails are processed and helping to prevent impersonation and fraud.
- Reporting: DMARC provides feedback reports to domain owners about the messages that pass and fail DMARC evaluation. These reports are crucial for understanding the domain's email ecosystem, identifying authentication issues, and spotting potential attacks.
- Improved Deliverability: By implementing DMARC, senders can signal to ISPs and email receivers that they care about email security. This can improve the chances of their emails being delivered as it indicates a proactive stance against email abuse.
Weaknesses of DMARC:
- Complexity and Maintenance: Setting up DMARC correctly requires understanding SPF and DKIM records and then creating a DMARC record that reflects the desired policy. Misconfiguration can lead to legitimate emails (also internal ones) being rejected or quarantined.
- Dependence on SPF and DKIM: DMARC requires both SPF and DKIM to be in place and properly configured to work effectively. This dependency means that organizations must invest time and resources in setting up and maintaining multiple authentication systems.
- Delayed Feedback: The feedback and reports provided by DMARC are not in real-time, which can delay response times to potential issues or attacks. This delayed feedback loop can be a challenge for timely incident response.
SPF vs DMARC
The main difference between SPF vs DMARC is that while SPF is a test that tries to verify the authenticity of who sent an email (using a list of mail servers that are allowed to send emails on behalf of a domain), DMARC is a rule that specifies what should happen if that verification fails.
DKIM vs DMARC
The main difference between DKIM vs DMARC is that while DKIM is a test that aims to verify the authenticity of an email message (using a digital signature), DMARC is a rule that specifies what should happen if that verification fails.
SPF vs DKIM
The main difference between SPF and DKIM is that while SPF uses a list of permitted mail servers to check the authenticity of where an email came from, DKIM uses a digital signature to check the authenticity of the email message itself.
DMARC vs DKIM vs SPF Summary:
- SPF verifies the sender's IP address.
- DKIM adds a digital signature to the email message.
- DMARC provides policy enforcement and reporting capabilities on top of SPF and DKIM.
Implementing all three authentication methods together provides the strongest defense against email spoofing and phishing attacks, helping to ensure the integrity of email communication and protect recipients from malicious emails.
For more information, read our email authentication 101, our guide on how to check your email authentication, and what to do about those annoying emails from noreply-dmarc-support@google.com.
Our Methodology
This article has been written and researched following our EmailTooltester methodology.
Our Methodology